Power Platform Plugin Managed Identity Certificate Flaw
On December 8, 2025, I reported a vulnerability (VULN-167837) to Microsoft regarding the managed identity implementation for Dataverse plugins. What I discovered was alarming: Power Platform only validates a partial certificate subject when authenticating managed identity federated credentials—a flaw that could allow unauthorized plugin execution. This follows my previous findings on Power Platform subnet delegation security risks.
What is Managed Identity for Dataverse Plugins?
Managed identity for Dataverse plugins is a feature that allows plugins to authenticate securely using Azure managed identities instead of traditional connection strings or credentials. According to Microsoft’s documentation, this approach enhances security by eliminating the need to store sensitive credentials in plugin code. The authentication relies on federated credentials that are configured to match the certificate subject used to sign the plugin assembly.
This feature is particularly important for organizations that need to maintain strict security compliance and want to leverage Azure’s identity management capabilities within their Power Platform solutions.
The Vulnerability: Partial Certificate Subject Validation
During my security testing, I discovered that Dataverse plugin validation only processes the first segment of a certificate’s subject field when validating federated credentials—ignoring everything after the first comma.
The Problem in Detail
My code signing certificate, issued by CERTUM (a trusted certificate authority), has the following subject:
Open Source Developer, Krzysztof Balcerowski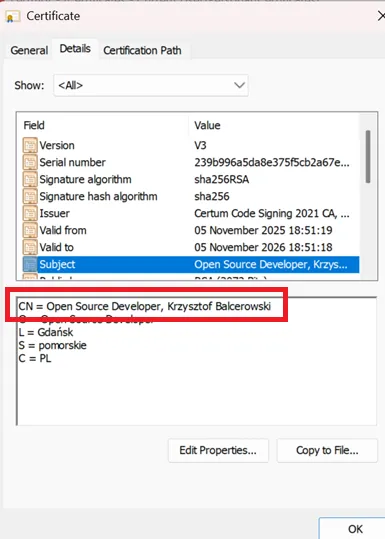
However, when configuring federated credentials according to Microsoft’s official documentation, the plugin execution fails at runtime. The error message revealed that Power Platform only recognized:
Open Source DeveloperThe system completely ignored my actual identifier: “Krzysztof Balcerowski.”
Here’s the part of actual error message from the runtime:
{
"error": {
"code": "0x80040265",
"message": "OrganizationServiceFault: Microsoft.Identity.Client.MsalServiceException: A configuration issue is preventing authentication - check the error message from the server for details. You can modify the configuration in the application registration portal. See https://aka.ms/msal-net-invalid-client for details. Original exception: AADSTS700213: No matching federated identity record found for presented assertion subject '/eid1/c/pub/t/<MY_TENANT_ID_REMOVED>/a/qzXoWDkuqUa3l6zM5mM0Rw/n/plugin/e/88b5e3c9-5cef-eb8d-bc15-d5c28a20d743/i/Certum Code Signing 2021 CA/s/\"Open Source Developer'. Check your federated identity credential Subject, Audience and Issuer against the presented assertion. https://learn.microsoft.com/entra/workload-id/workload-identity-federation"
}
}Notice the critical detail in the error message: the subject field ends with s/\"Open Source Developer' — the system truncated the certificate subject at the first comma, dropping “Krzysztof Balcerowski” entirely.
Note: Code signing certificates issued by trusted certificate authorities like CERTUM are commonly used by open-source developers and contain professional identifiers in the subject field. The comma-separated format is standard practice for including multiple identification attributes.
Why This Matters
This parsing flaw creates a potential security risk: if multiple developers or organizations share certificates with identical first segments in their subject fields (e.g., “Open Source Developer, Alice” and “Open Source Developer, Bob”), the system cannot properly distinguish between them.
The security implications include:
- Lack of proper certificate identity verification: The system cannot uniquely identify certificate holders when subjects contain commas
- Potential for credential confusion: Certificates with matching first segments might be incorrectly validated
- Violation of the principle of least privilege: The authentication mechanism is less precise than intended by the certificate authority’s naming structure
- Compliance concerns: Organizations in regulated industries may fail audits if certificate subject validation is incomplete
Reproduction Steps
To reproduce this vulnerability, follow these steps:
-
Create a managed Power Platform environment with managed identity support enabled
-
Prepare a Dataverse plugin that uses managed identity authentication
-
Obtain a code signing certificate from a trusted authority (such as CERTUM, DigiCert, GlobalSign, etc.) where the certificate subject contains comma-separated values (e.g.,
Open Source Developer, Your Name) -
Sign your NuGet package/plugin with this certificate following standard code signing procedures
-
Configure federated credentials following the official Microsoft documentation, using your complete certificate subject as specified in your certificate details
-
Deploy and execute the plugin in your managed environment
Expected vs. Actual Behavior
Expected: The system should validate the complete certificate subject: Open Source Developer, Krzysztof Balcerowski
Actual: The plugin throws an exception indicating invalid federated credentials. The error message reveals that the system only recognizes Open Source Developer—truncating everything after the first comma.
The error message explicitly instructs you to configure the federated credential with only the partial subject, confirming that the platform is deliberately processing only the first segment.
Impact Assessment
This vulnerability affects:
- Enterprise developers using comma-separated certificate subjects from commercial certificate authorities
- Open-source contributors who use certificates with professional designation formatting
- Organizations sharing similar certificate naming conventions
- Compliance-focused environments where precise identity verification is mandatory
The severity is low to high depending on your certificate naming and organizational structure. While the flaw doesn’t directly expose credentials, it undermines the integrity of the identity verification process.
Real-World Attack Scenario: Malicious ISV Impersonation
To understand the practical exploitation of this vulnerability, consider the following attack scenario involving Independent Software Vendors (ISVs) in the Power Platform ecosystem.
The Attack Vector
Imagine two ISVs with code signing certificates from the same certificate authority:
Legitimate ISV (Target):
- Company: “Contoso Solutions Ltd”
- Certificate Subject:
Power Platform Developer, Contoso Solutions Ltd - Established reputation in the Power Platform community
- Has existing customer base with configured federated credentials
Malicious ISV (Attacker):
- Company: “Malicious Corp”
- Certificate Subject:
Power Platform Developer, Malicious Corp - Obtains a valid code signing certificate from the same or different trusted authority
- Deliberately crafts the subject to match the first segment of the legitimate ISV’s certificate
The Attack Flow
-
Certificate Acquisition: The malicious ISV obtains a legitimate code signing certificate from a trusted certificate authority with a carefully crafted subject that matches the first segment of a known legitimate ISV:
Power Platform Developer -
Plugin Development: The attacker develops a malicious Dataverse plugin that appears legitimate (e.g., “Enhanced Analytics Tool” or “Security Compliance Checker”) but contains malicious code designed to:
- Exfiltrate sensitive Dataverse data
- Establish persistence in the customer’s environment
- Modify business logic or data
- Create backdoor admin accounts
-
Social Engineering: The malicious ISV uses social engineering tactics to convince customers to install their plugin:
- Impersonating the legitimate ISV through phishing emails
- Offering “discounted” or “trial” versions of popular solutions
- Exploiting trust in the Power Platform AppSource ecosystem
- Targeting customers who already use similar solutions from legitimate ISVs
-
Federated Credential Confusion: Here’s where the vulnerability becomes critical. If the customer has already configured federated credentials for the legitimate ISV’s plugin (with subject
Power Platform Developer, Contoso Solutions Ltd), the malicious plugin can exploit the partial validation:- The Azure-side federated credential configuration remains unchanged (already exists from the legitimate plugin setup)
- When the malicious plugin executes, Power Platform only validates
Power Platform Developer - The system cannot distinguish between the legitimate ISV’s certificate (
Power Platform Developer, Contoso Solutions Ltd) and the malicious ISV’s certificate (Power Platform Developer, Malicious Corp) - The malicious plugin automatically gains the same level of trust without any additional configuration required from the customer
- If the attacker modifies an existing open-source plugin and re-signs it with their certificate (matching the first segment), convinces the customer to install the “updated” plugin package, it can execute immediately with the existing federated credentials—no additional configuration needed
-
Exploitation: Once installed and configured, the malicious plugin executes with managed identity credentials, potentially gaining access to:
- Customer’s Dataverse data and business logic
- Azure resources configured for managed identity access
- Integration endpoints configured in the federated credential setup
Why This Attack Works
The flaw enabling this attack is the incomplete certificate subject validation. In a properly implemented system:
- The full certificate subject should uniquely identify the ISV
Power Platform Developer, Contoso Solutions Ltd≠Power Platform Developer, Malicious Corp- Federated credentials should reject any certificate that doesn’t match the complete configured subject
However, with the current implementation:
- Both certificates are treated as equivalent because they share
Power Platform Developer - Customers cannot configure granular trust boundaries based on complete certificate identity
- The security model degrades to trusting any certificate with a matching first segment
Likelihood and Mitigation
While this attack requires specific conditions (matching first segments, social engineering success, and customer misconfiguration), it represents a real threat because:
- Common certificate naming patterns exist: Many developers use similar professional designations like “Power Platform Developer,” “Microsoft Developer,” “Certified Developer,” etc.
- Certificate authorities don’t prevent duplicate first segments: There’s no central registry preventing multiple entities from using the same professional designation
- Customers trust valid certificates: A plugin signed by a legitimate certificate authority appears trustworthy, even if the ISV is malicious
- The error message guides exploitation: When the system instructs administrators to use only the first segment, it actually teaches them to configure the vulnerability
Defense strategies:
- Verify the complete certificate subject manually before configuring federated credentials
- Only install plugins from verified, reputable ISVs with established track records
- Implement additional monitoring and auditing of plugin behavior in production
- Maintain an allowlist of trusted certificate subjects (using the full subject, not just the first segment)
Workarounds
Until Microsoft addresses this vulnerability, consider these workarounds:
-
Use certificates with single-segment subjects (no commas in the subject field) when signing plugins intended for managed identity authentication
-
Ensure unique first segments if you must use comma-separated subjects in your organization—avoid generic prefixes like “Developer” or “Engineer”
-
Implement additional validation layers in your plugin code to verify the executing context matches expected identity attributes
-
Document the limitation in your security procedures and conduct regular audits to ensure certificate subjects remain unique at the first-segment level
Microsoft’s Response
I received the following response from the Microsoft Security Response Center (MSRC):
Hello,
Thank you again for submitting this report to the Microsoft Security Response Center (MSRC).
After careful investigation, this case has been assessed as Low severity and does not meet Microsoft’s bar for immediate servicing for the following reasons:
- No certs currently in production has ’,’ within the subject or issuer’s common name. Thus, its not an active vulnerability for plugin ppmi. None of customer’s plugin in production can be exploited currently.
- Environment id is stamped within the FIC, thus the vulnerability can not be configured for cross tenant resource access.
Nevertheless, we have shared the report with the team responsible for maintaining the product or service. They will take appropriate action as needed to help keep customers protected.
MSRC prioritizes vulnerabilities that are assessed as an Important or Critical severity. Since this case was below the bar for immediate servicing, it is not eligible for bounty, and no CVE will be issued. MSRC will not be tracking this issue further, and no additional updates will be provided.
Analysis of Microsoft’s Response
While I appreciate Microsoft’s review, I believe their assessment misses the valid attack scenario outlined in this article. Let me address their points:
Regarding Point 1: “No certs currently in production has ’,’ within the subject”
This argument is fundamentally flawed for several reasons:
- My certificate proves otherwise: I have a legitimate production certificate from CERTUM (a trusted certificate authority) with a comma-separated subject. The existence of my certificate alone contradicts this claim. Maybe they only checked production Power Platform environments I do not know.
- Certificate authorities actively issue these certificates: Major certificate authorities like CERTUM, DigiCert, and others regularly issue code signing certificates with comma-separated subjects for professional designations.
- Security by obscurity is not security: The fact that such certificates may not be widely used today doesn’t mean the vulnerability should be ignored. Security vulnerabilities should be addressed based on their potential impact, not current exploitation statistics.
- Forward-looking security: As managed identity adoption grows, more developers will encounter this issue, and the attack surface will expand.
Regarding Point 2: “Environment id is stamped within the FIC, thus the vulnerability can not be configured for cross tenant resource access”
Microsoft’s response focuses on cross-tenant attacks, but this completely misses the same-tenant impersonation scenario I described:
- The attack I outlined is not cross-tenant—it occurs within the same customer tenant
- The scenario involves a malicious ISV convincing a customer to install a plugin that exploits existing federated credentials already configured in that customer’s tenant
- Because the environment ID is included in the federated identity credential (FIC), the malicious plugin executing in the same environment can leverage the partial certificate subject validation to gain unauthorized access
- The vulnerability enables ISV impersonation, not cross-tenant access
The Real Risk Microsoft Overlooked
The attack vector is this:
- Customer configures federated credentials for a legitimate plugin signed with certificate subject:
Power Platform Developer, Contoso Solutions Ltd - Malicious actor obtains a certificate with subject:
Power Platform Developer, Malicious Corp - Through social engineering, the attacker convinces the customer to install their malicious plugin (or an updated version of an open-source plugin)
- The malicious plugin executes in the same tenant, same environment with the existing federated credentials
- Power Platform only validates
Power Platform Developerand cannot distinguish between the two certificates - The malicious plugin gains the same access as the legitimate one—no cross-tenant attack required
This is a same-tenant credential confusion attack, not a cross-tenant attack. The environment ID protection Microsoft mentions is irrelevant because the attack occurs within the customer’s own environment.
Implications
Microsoft’s decision to classify this as “Low severity” and not track it further is concerning, especially given:
- The fundamental flaw in certificate validation logic that violates security best practices
- The potential for ISV impersonation attacks within customer tenants
- The precedent this sets for incomplete identity verification in Power Platform security features
- The pattern of Microsoft dismissing Power Platform security concerns (as seen with my previous subnet delegation report)
As with my subnet delegation security gap report that remains unaddressed after one year, it appears this limitation will persist. Organizations implementing managed identity for plugins should be aware of this risk and implement the workarounds outlined in this article.
Final Thoughts
This discovery highlights a concerning pattern in Power Platform’s security implementation: fundamental identity validation mechanisms that don’t properly handle standard certificate formats. While managed identity is promoted as a more secure alternative to traditional authentication methods, incomplete certificate subject validation undermines this promise.
The fact that the platform explicitly tells developers to use the truncated subject (rather than throwing an error about an unsupported format) suggests this is a deliberate design decision rather than an oversight. However, this design conflicts with certificate authority standards and creates security gaps in identity verification.
For organizations evaluating managed identity for Dataverse plugins, carefully review your certificate naming conventions and consider whether this limitation impacts your security posture. If your compliance requirements mandate complete certificate subject validation, you may need to reconsider this authentication approach until Microsoft resolves the issue.
What are your thoughts on this vulnerability? Have you encountered similar certificate validation issues in Power Platform or other Microsoft services? I’d love to hear your experiences in the comments.